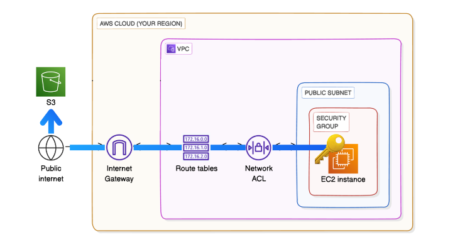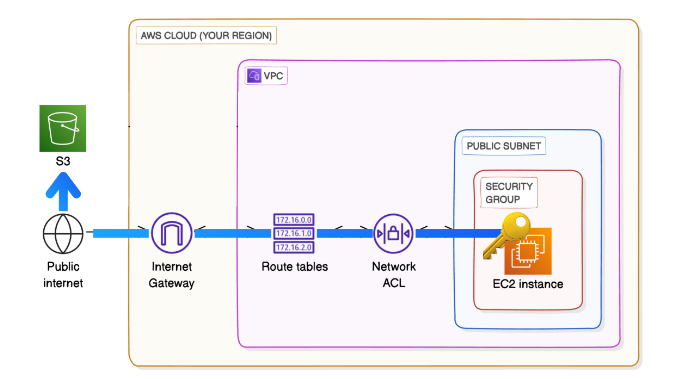
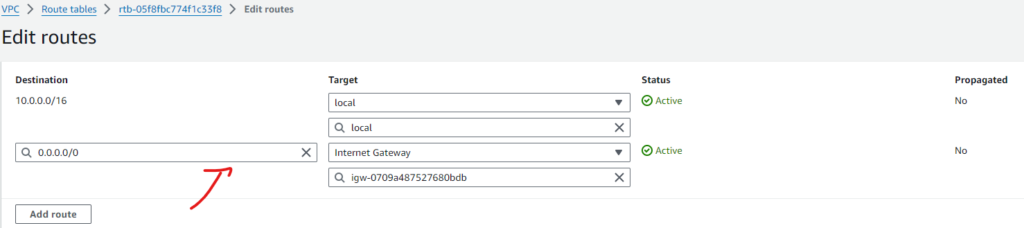
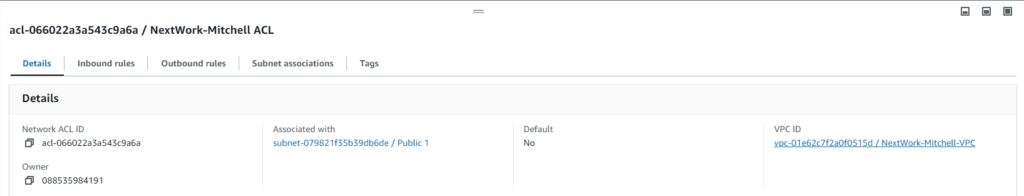
After we setup our basic VPC and add our Subnet. We add a route from the route table. Then we create our Security Group and ACL. Our Subnet, Route, Security Group, and ACL are all connected so that we can attach it to our Internet Gateway.
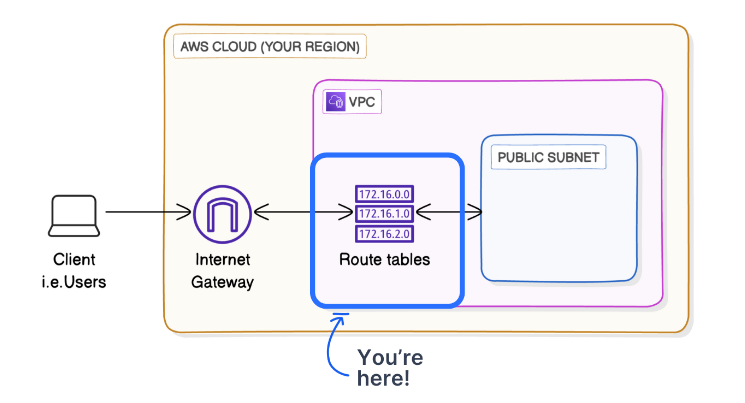
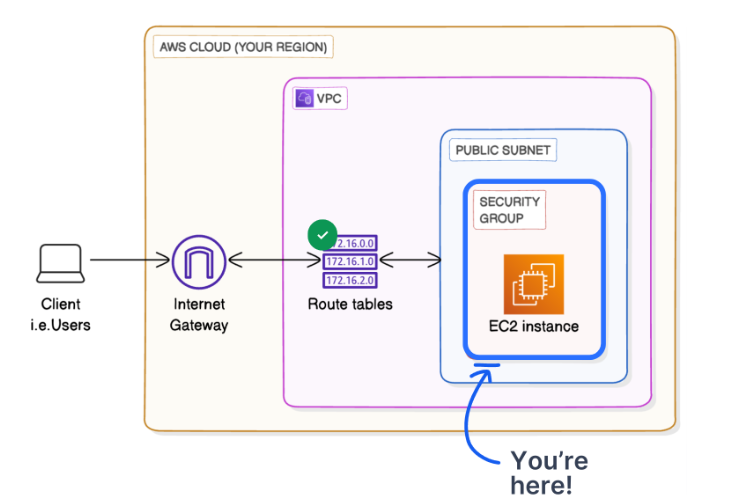
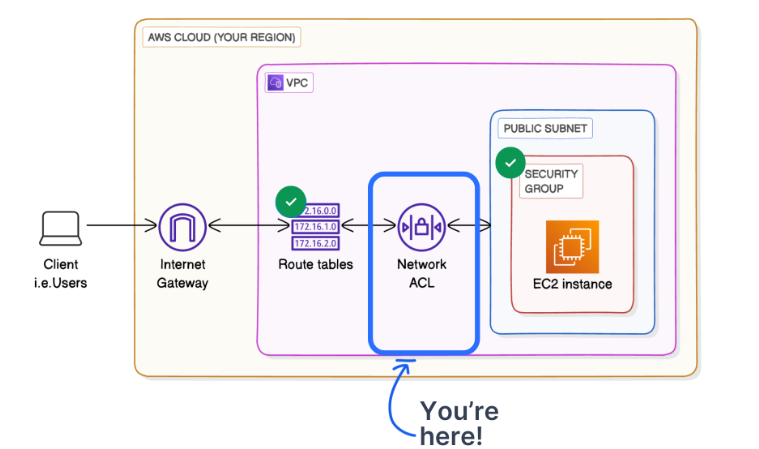
This is what it looks like in a diagram:
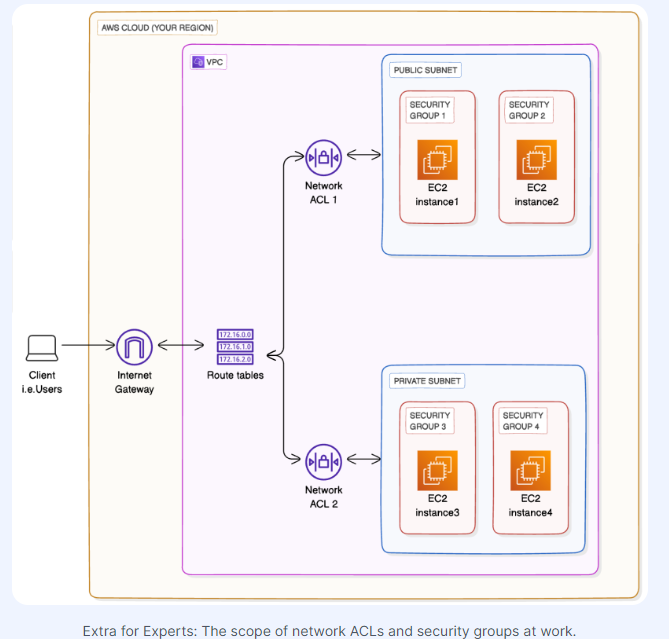
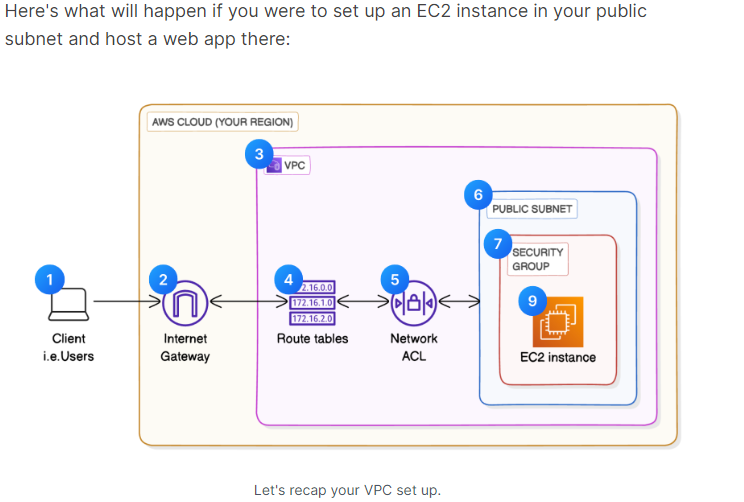
Here’s what will happen if you were to set up an EC2 instance in your public subnet and host a web app there:
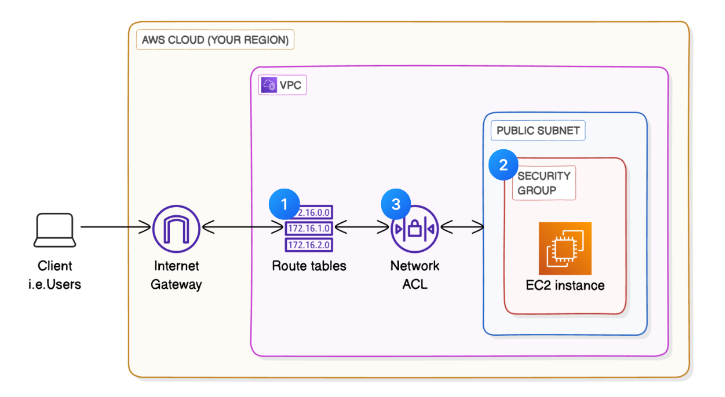
- 💻 Client/User: A user enters the URL of your website into their web browser and hits enter.
- 🚪 Internet Gateway: The request (in the form of data packets) is sent from the user’s browser through the internet and reaches the Internet Gateway (IGW) associated with your VPC, NextWork VPC.
- 🌐 VPC: The Internet Gateway forwards the user’s request into your Virtual Private Cloud (VPC), NextWork VPC.
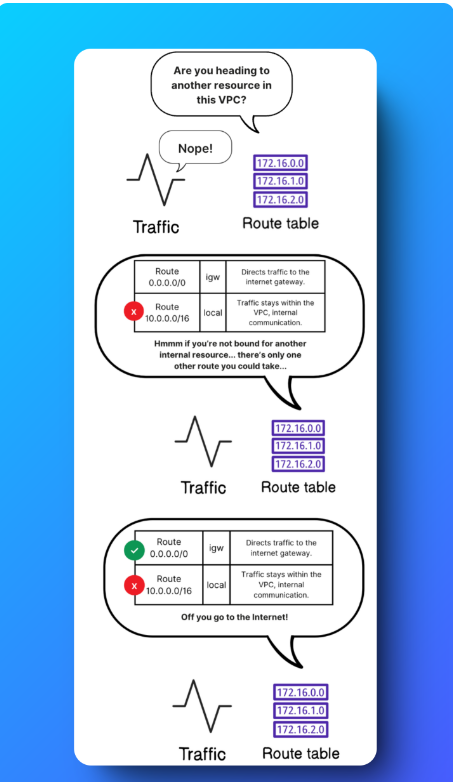
- 🚏 Route Table: Your VPC has a route table for your public subnet (called NextWork route table), which directs the traffic locally to your EC2 instance hosting the website. The data packets get put on the local route in the route table.
- 📋 Network ACL: While en route to your EC2 instance, the request has to pass through the network ACL associated with your public subnet. The network ACL has an inbound rule to allow all inbound traffic (Inbound Rule 100 allows all inbound traffic i.e. 0.0.0.0/0), so your request is let through.
- 🥅 Public Subnet: The request enters your public subnet Public 1, where your EC2 instance is located.
- 👮♀️ Security Group: The request reaches the security group NextWork Security Group attached to the EC2 instance. The security group checks its inbound rules to allow or deny the request based on the IP address, protocol, and port. The security group has an inbound rule that allows HTTP traffic (Port 80) from anywhere (0.0.0.0/0).
- 😮💨 EC2 Instance: The request reaches your EC2 instance hosting the website. The web server on the EC2 instance processes the request and prepares the response.
- Data gets sent back: The response data from the EC2 instance i.e. website content is sent back to the user. The outbound traffic goes through the security group, public subnet, network ACL, route table, VPC, and Internet Gateway, finally reaching the user’s browser, displaying the website content. Amazing work!
Lets Recap
Today you’ve learnt how to:
- 🚏 Set up route tables: You configured a route table in your VPC to send Internet-bound traffic to your internet gateway, turning your subnet into a public subnet.
- 👮♀️ Implement security groups: You created a security group to control inbound and outbound traffic at a resource level, specifying allowed IP addresses, protocols, and ports.
- 📋 Deploy network ACLs: You set up network ACLs as an additional layer of security, managing both incoming and outgoing traffic at the subnet level.