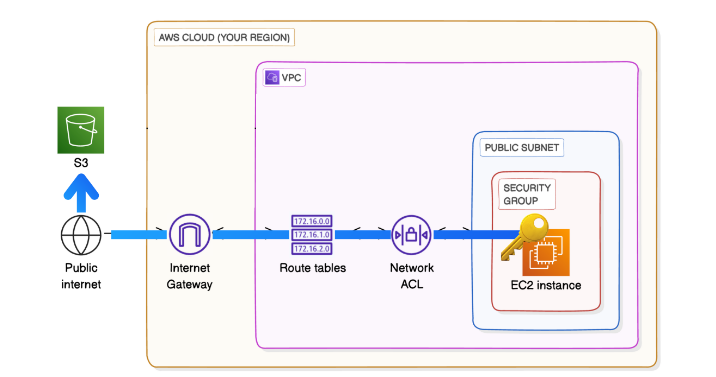
VPC Endpoints are your answer!
VPC Endpoints let your VPC privately connect to AWS services without needing to go through the internet.
You can look at the following resources if you need a refresher on topics:
- https://mmoorewebdev.com/making-our-first-vpc-on-aws/
- https://mmoorewebdev.com/cloud-security-with-aws-iam/
- https://mmoorewebdev.com/aws-vpc-traffic-flow-security/
- https://mmoorewebdev.com/launching-vpc-resources-in-aws/
- https://mmoorewebdev.com/how-to-securely-test-your-vpc-connectivity/
- https://mmoorewebdev.com/how-to-securely-access-s3-from-a-vpc/
Here’s a hands-on project I did to create a VPC endpoint:
☁️ Set up a VPC with an EC2 instance and endpoint.
🪣 Launched an S3 bucket that only allows traffic from my endpoint.
🚪 Used route tables to direct s3-bound traffic from my EC2 instance to my endpoint.
🧪 Validated my endpoint setup by using my EC2 instance to run CLI commands.
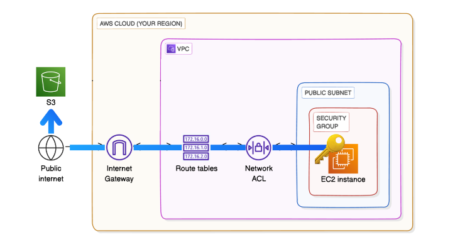
After going through the step by step below, this is what the overview will look like:
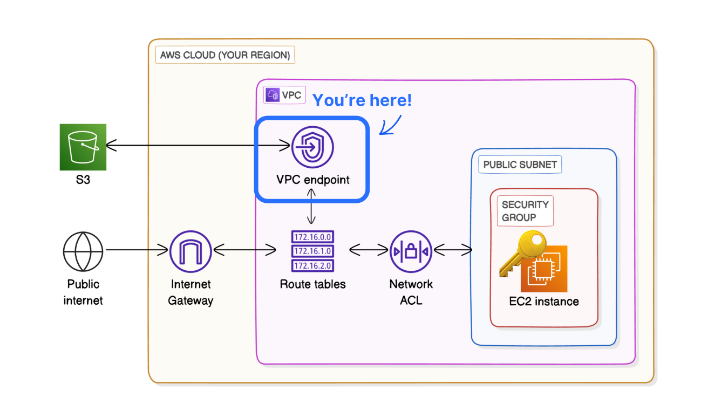
Finally, After going through the step by step, you would have learned how to:
🚪 Set up a VPC endpoint: You created a VPC endpoint that enables secure, direct access from your VPC to S3. The type of endpoint you set up was an S3 Gateway.
🪣 Manage permissions with bucket policies: You set up a strict bucket policy that blocks off all access to your bucket, except for access from your VPC endpoint.
👩🔧 Resolve VPC endpoint issues: You resolved connectivity issues by adding a route that directs S3-bound traffic from your public subnet to your S3 Gateway endpoint!